NepCTF-2025

WEB-easyGooGooVVVY
提示说groovy表达式注入
上网搜搜



1 | package com.al1ex; |
WEB-RevengeGooGooVVVY

和上题一样的payload

1 | package com.al1ex; |
WEB-JavaSeri
提示为Shiro,找个工具一把梭

MISC-NepBotEvent
ai出的


1 | from struct import unpack |

MISC-客服小美
题目有一个流量与一个内存文件
流量看了一眼非常明显的cs特征

使用LovelyMem挂载镜像

发现了木马文件(顺路得到了用户名)
查看网络连接,发现了他的网络连接

接下来就是秘密文件了
获取beacon
过滤一下http流量

这个/TJvI就是获取beacon的URL会返回beacon文件

1 | characters = 'TJvI' |
93对应为x64 ,92为x86,说明这个beacon是x64的
网上有脚本可以分析这个stagebeacon
https://github.com/minhangxiaohui/CSthing
导出文件然后执行脚本

可以看出cs版本位4.4(伏笔
由于我们没有.cobaltstrike.beacon_keys文件无法直接获取私钥,虽然信标有公钥可以得到n,但是yafu爆不出n的两个p与q,所以也无法间接得到私钥,
因此可以利用动态信标的进程转储直接获得 AES key、HMAC key,不需要去破解私钥解密元数组了
3.x版本文件中能找到未加密的元数组,并且是以 0x0000BEEF 开头的字节序列。同时在进程的生命周期中越早获取进程转储,它就越有可能包含未加密的元数据。4.x 基本不能从动态信标的进程转储文件中恢复未加密的元数组,也就是说直接对 4.x 版本 cs 的动态信标的进程转储文件是提取不出通信所需要的 key。4.x 有自己解密的方法:
AES 和 HMAC 密钥可以在可写进程内存中找到,但没有明确标识这些密钥的标头。它们只是 16 字节长的序列,没有任何可区分的特征。为了提取这些密钥,该方法包括执行一种字典攻击。在进程内存中找到的所有可能的 16 字节长、非空序列将用于尝试解密一段加密的 C2 通信。如果解密成功,则已找到有效密钥。 该解密方法除了需要动态信标的进程转储文件之外还需要加密数据
首先先用上文提到的 cs-parse-http-traffic.py 脚本对抓取的流量包进行提取加密数据的操作
1 | python.exe .\cs-parse-http-traffic.py -k unknown .\DESKTOP.pcapng |

得到加密数据之后,再用动态信标的进程转储文件进行爆破解密,得到 key
进程转储文件由镜像中导出

1 | python.exe .\cs-extract-key.py -t ecfff639c9a79bbb3c59bbec390fa070335fa6d5b33c7ba752fe9803ee2082296233a5dcd7f76c8adb3a1e404df09447 .\minidump_pid_6492.dmp |

1 | AES Key: a6f4a04f8a6aa5ff27a5bcdd5ef3b9a7 |
拿到AES_KEY、HMAC_KEY后可以直接用以下这个脚本来解密数据,往encrypt_data填入加密数据,就能解密数据
1 | import hmac |


1 | NepCTF{JohnDoe_192.168.27.132:12580_5c1eb2c4-0b85-491f-8d50-4e965b9d8a43} |
MISC-SpeedMino
说分数到2600即可得到flag,但是没有(骗人)
根据题目speed改我们的速度发现可以得到flag

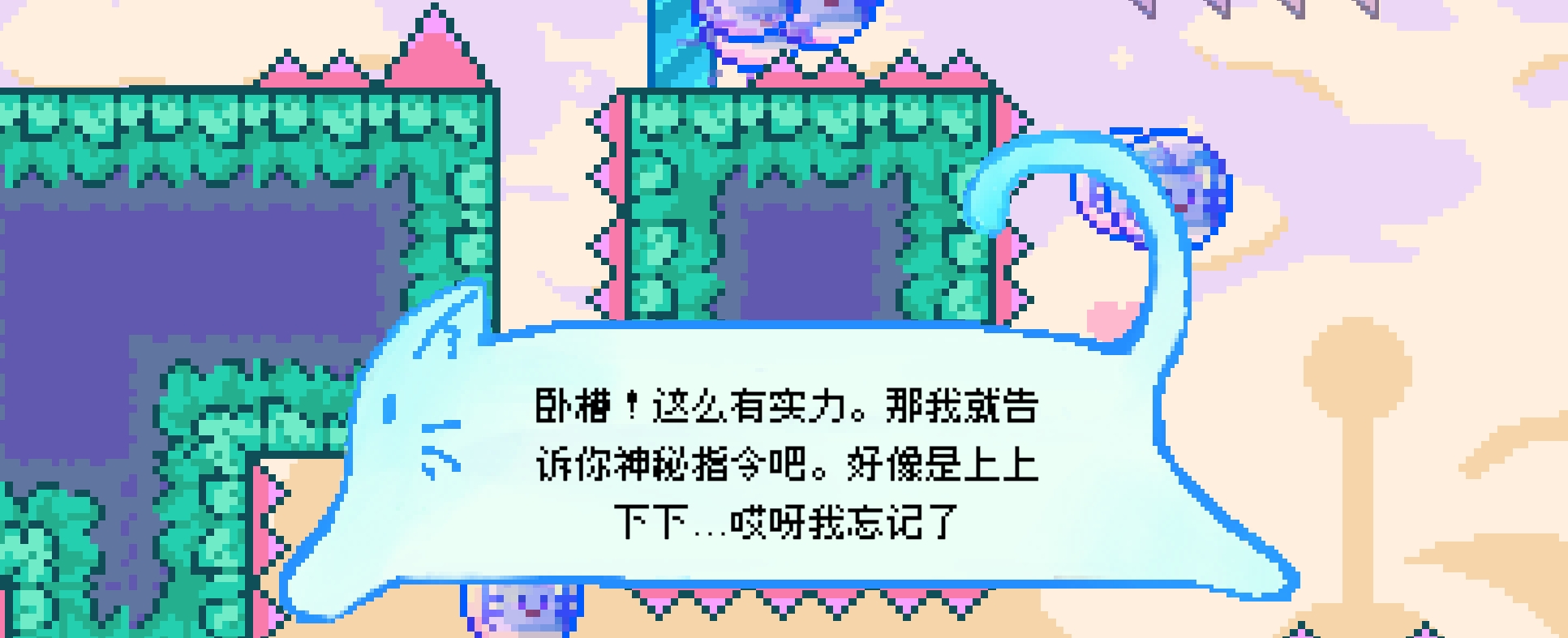
MISC-MoewBle喵泡


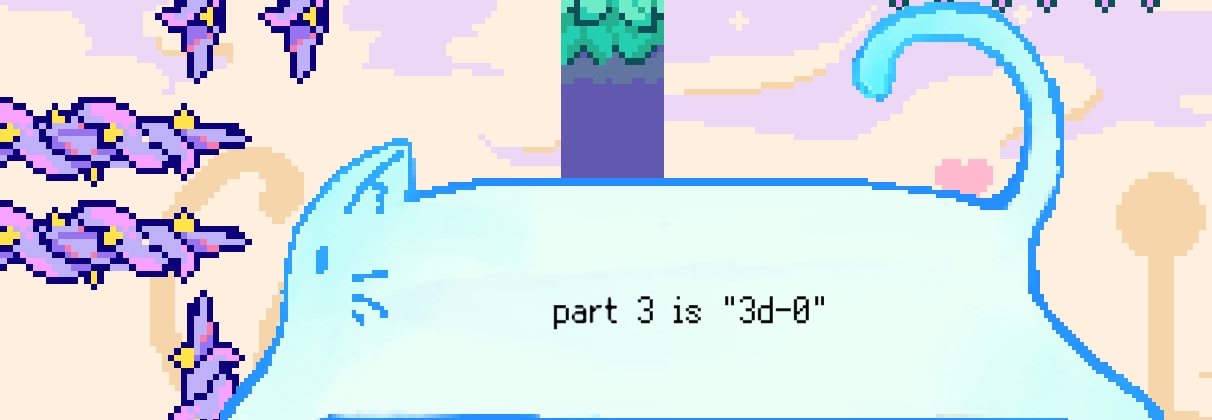
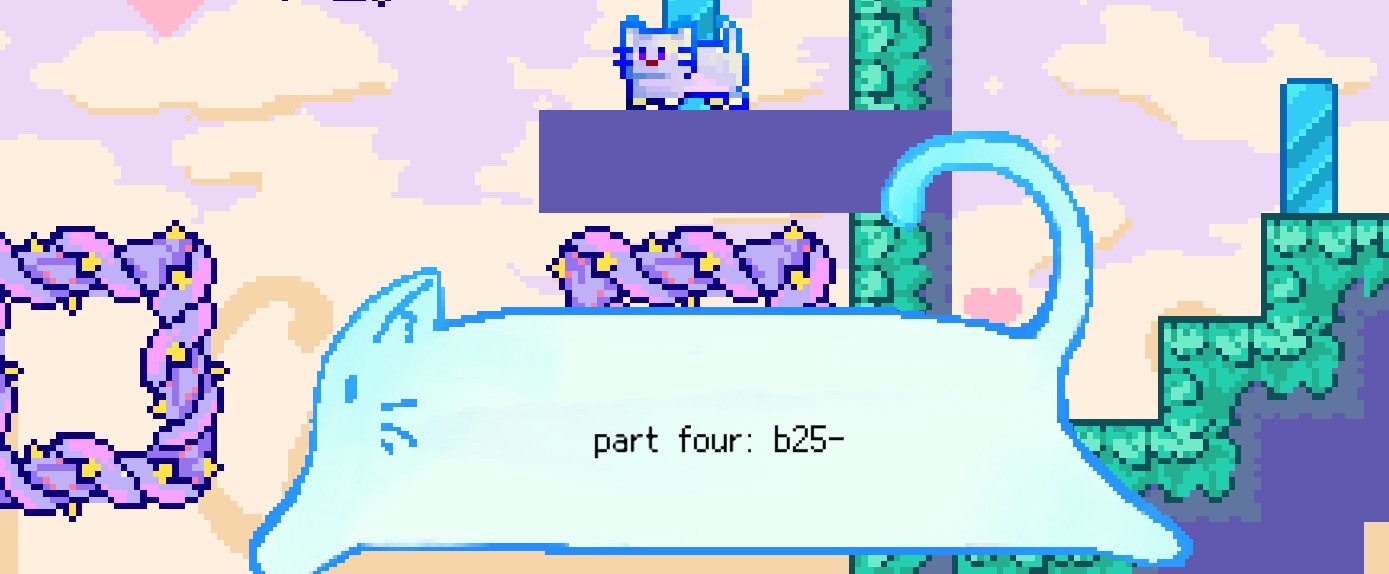



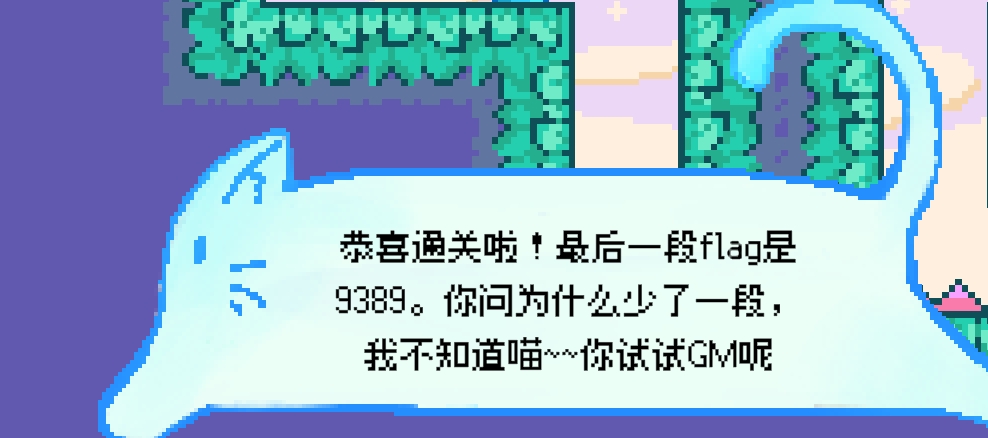
还有一个告诉神秘面板,为暂停面板
魂斗罗gm,上上下下左右左右ba


MISC-问卷!!!

RE-Crackme

通过前端可以拿到密钥啥的,让ai写个脚本解密我们发送的密文


我们尝试发送一个空的payload


得到flag
猜测后端逻辑:将解密后的数组存放在一个数组中,提取每一个键与键值,若有误exit,无误continue,由于我们为空,所以就畅通无阻的来到了代码末尾,得到flag
RE-Realme

找到main



推测为魔改rc4
在编写解密脚本时发现出来的是乱码
推测进行了反调试修改数据
在翻找时发现两个函数


一个是用peb来检测,另一个是通过closehandle来反调试
patch掉反调试后动调查看rc4逻辑
sbox多异或了两次
最后的异或换成了加减法
编写代码解密
1 | #!/usr/bin/env python3 |
Crypto-Nepsign
密码就是deepseek与chatgpt做的,跟我关系不大了
1 | from pwn import * |


Crypto-Lattice Bros
1 | from sage.all import * |


- 标题: NepCTF-2025
- 作者: tiran
- 创建于 : 2025-07-28 16:40:51
- 更新于 : 2025-07-28 16:41:14
- 链接: https://www.tiran.cc/2025/07/28/NepCTF-2025/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。